ATO governance needs reform: IPA-Deakin SME Research Centre
The IPA-Deakin SME Research Centre has examined the shortcomings of the ATO’s governance model and proposed a Tax...
READ MORE
In April, Public Accountant created a self-guided quiz to help readers benchmark their level of cybersecurity protection. We’ve collected the results, and asked a cybersecurity expert what you should do next.

Assistant Treasurer and Minister for Financial Services the Hon Stephen Jones MP this week shared a warning about common tax-time scams.
“Impersonation scams are mostly commonly seen at tax time,” Jones said. “Scammers will impersonate the ATO contacting individuals via a link to a fake myGov login page.”
Other common scams, Jones said, generally seek personal information via phone calls, private messages on social media, email or text. Scammers might pose as the ATO on social media to offer help with tax and super questions, or notify people of fake refunds, before attempting to gather as much personal information as possible.
Consumers need to educate themselves about the risks, and accountants have a role to play in educating their clients. Accounting professionals also need to know how to identify false information, and be familiar with what to look out for in their own inboxes. Cybersecurity risks and security measures should be front of mind for accountants.
Public Accountant released a self-guided quiz earlier this year to help readers assess their level of cybersecurity protection.
We’ve collected the results to shine a light on areas that need more attention, and asked Prashant Haldankar, Chief Information Security Officer at Sekuro, to suggest some starting points for improvement.
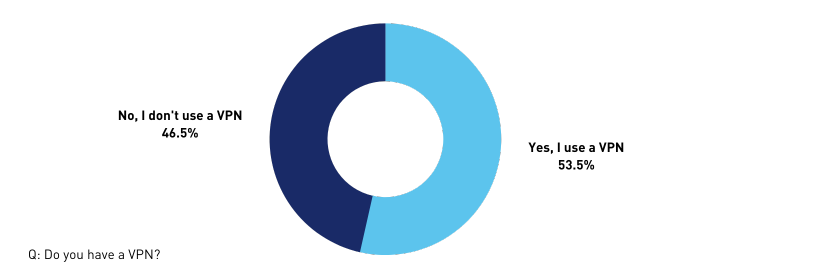
Forty-seven per cent of respondents don't have a VPN.
This is cause for concern, said Haldankar, as a VPN provides a basic level of protection.
“It’s how you log in securely to your trusted network and access confidential resources that you’ve been allowed to access,” said Haldankar. “When the pandemic hit, many organisations were not ready with remote access through a VPN. Surprisingly, many organisations are still putting together systems to enable secure access for remote workers.”
One critical point is to continually update your level of cybersecurity protection, including VPN access.
“It’s not a point-in-time exercise. It needs to be regularly reviewed and updated to ensure you have the right protection for your organisation.”

Eighty-four per cent of respondents use detection software, such as anti-malware, authentication logs and phishing email filters, to detect malicious activity.
Haldankar isn’t surprised that organisations are fairly mature in this domain due to widespread discussion about the risks in email and internet access in the early 2000s.
“Education about the first line of defence was very prevalent when we started having more conversations about cybersecurity,” said Haldankar. “Email content filtering and web access controls were considered basic security requirements. Those technologies were heavily leveraged.”
Nowadays, newer technologies such as AI tools are built into email to flag potential phishing attempts.
Those AI tools, explained Haldankar, are based on behavioural testing.
“For example, it will look at the pattern of how I write emails and, if it detects something abnormal, it will identify where it’s coming from.”
Once the first line of defence has been compromised, attackers will attempt to reach further into an organisation.
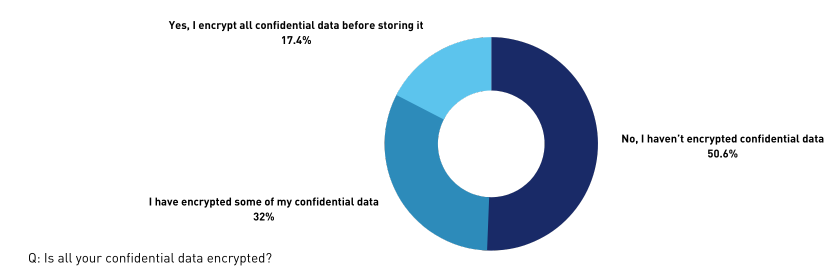
That’s why encrypting confidential data is critical – something that just over half (51.3%) of respondents say they do.
“Attackers’ main objective is to get to an organisation’s critical data. Encryption makes it difficult for the attacker to access the encrypted information.”
Similar to multifactorial authentication, encrypting data has become commonplace, so Haldankar is surprised that around half of respondents haven’t yet taken this step.
“It’s an essential foundation of cybersecurity. Your critical data should be encrypted. Many organisations are also encrypting their end devices such as mobile phones and laptops. Because you deal with so much information locally on laptops as well.”
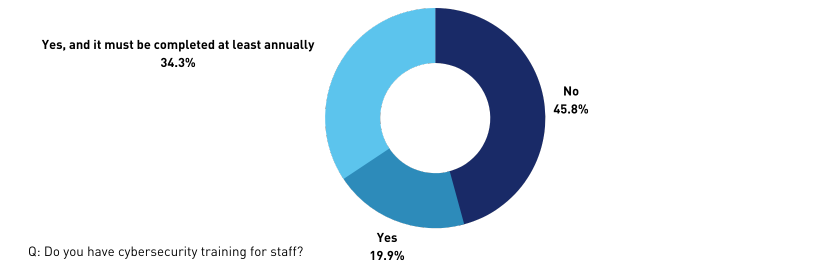
Forty-six per cent of respondents don’t have cybersecurity training available for staff.
Haldankar believes organisations often hold back from rolling out cybersecurity training because of the perception that it’s highly technical.
“They think it’ll be a large and complex exercise to get trained in cybersecurity, but cyber-awareness does not need to come hand-in-hand with extra technical expertise,” he says.
The same applies to cybersecurity champions in a particular team or department.
“Basic education and training can be enough to give a champion in each business unit the knowledge to stop an attack before it happens. When a staff member gets something unusual that could be a cyberattack, they should be equipped with some basic information to detect and report it to a cybersecurity expert.”
He also emphasises that training should to be up-to-date.
“[Training] goes a long way in building cybersecurity capabilities within an organisation to detect those attacks and try to avoid them in the very early stages.”
It’s not just employees, but also partners, clients and suppliers, who can benefit from cybersecurity awareness.
“Organisations should share their defence strategy and create awareness. A lot of incidents occur at the supplier level rather than in the organisation itself.”
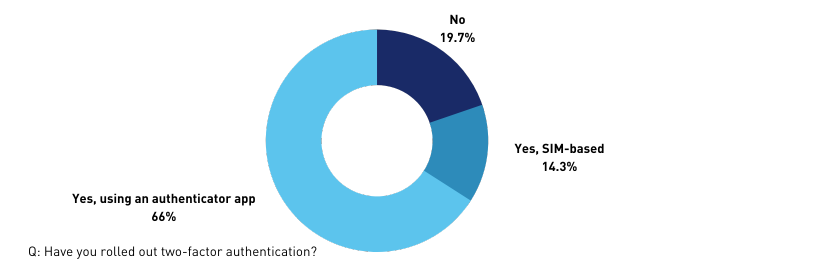
Multifactorial authentication is becoming the norm, said Haldankar, so it's little surprise that 66% of respondents have rolled out two-factor authentication.
“Many organisations have taken it on as a standard way of accessing the network. It’s not costly technology and we should be urging organisations to adopt multi-factor authentication to access the network, not only remotely, but locally as well when they’re in their offices.”
For those organisations that haven’t rolled out multifactorial authentication, or are evaluating the effectiveness of their current processes, Haldankar recommends creating a comprehensive cybersecurity plan that takes into account an organisation’s level of risk.
“You need to measure, identify and evaluate where the sensitive data resides, what the intellectual property, existing technology systems and processes are, as well as the level of cyber-awareness among staff and contractors.”
The level of authentication (ie, if you have two or more levels of authentication) required will depend on the sensitivity of the data and the risks posed in your organisation.
“Conduct an assessment and create a defence plan. There are also technical solutions suited to an organisation’s risk appetite. Any cybersecurity plan should be looked at holistically.”
Note: This quiz was answered by members across IPA group in Australia, the UK and elsewhere around the world.
Learn how to improve your cybersecurity through our on-demand webinar 14 ways to protect your business from a cyber attack.